Computer Security Threat Monitoring And Surveillance | by James P. Anderson
This is the "final report" of a study, the purpose of which was to improve the computer security auditing and surveillance capability of the customer's systems.
| Title | Computer Security Threat Monitoring And Surveillance |
| Author | James P. Anderson |
| Publisher | James P. Anderson Co. |
| Year | 1980 |
| Copyright |  |
 Background
Background- Audit trails are taken by the customer on a relatively long term (weekly or monthly) basis. This data is accumulated in conjunction with normal systems accounting programs. The audit data is derived f...
 Threats
Threats- Scope In order to design a security monitoring surveillance system, it is necessary to understand the types of threats and attacks that can be mounted against a computer system, and how these threa...
 Gaining Access To The System - External Penetration
Gaining Access To The System - External Penetration- In the context of this report, the term external penetration1' is not confined to the usual case of an outsider attempting to gain access to a computer resource in an organization of which he is not ...
 Internal Penetration
Internal Penetration- In many installations, the internal penetration is more frequent than external penetrations. This is true for a variety of reasons, not the least of which is the internal penetrator has overcome a maj...
 Clandestine User Countermeasures
Clandestine User Countermeasures- The penetration issue is one which can be played measure - countermeasure through what appears to be endless variations* What is really at the heart of the difficulty of defense is the fact that the...
 Characterization Of Computer Use
Characterization Of Computer Use- Introduction The basic premise of this study is that it is possible to characterize the use of a computer system by observing the various parameters available through audit trails, and to establish...
 Time Parameters
Time Parameters- There are basically 2 time parameters of interest that characterize how a system is used for a particular job. The first of these is the time of day (and in a larger sense the day of the week) that a ...
 Structure Of A Surveillance System
Structure Of A Surveillance System- Introduction This section outlines the functional components of a security monitoring and surveillance system. It identifies the key programs that will be required and considers a number of alterna...
 Monitoring Files
Monitoring Files- Producing the records necessary to monitor use of files or other objects in a system is similar to that outlined above for monitoring users activities in a system. The principal difference is that fac...
 Adapting To SMF Data. Relevant SMF Records
Adapting To SMF Data. Relevant SMF Records- The principal SMF records of use in performing the kind of auditing discussed in the preceding sections are record types 4, 5, 6, 10, 14, 15, 17, 18, 20, 25, 26, 34, 35, 40, 62, 63, 64, 67, 68, 69, 80...
 Other Surveillance Tools
Other Surveillance Tools- It is -understood that the customer's SMF data is kept on-line for one day and then written out to tape(s) for longer-term storage. In addition to the standard exception reporting program outlined in ...
 Development Plans
Development Plans- Introduction This section outlines a development plan and gives an estimated schedule and-level of effort to provide an operationally useful security surveillance system. No serious attempt has bee...
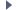 Surveillance Subsystem Functional Description
Surveillance Subsystem Functional Description- The Surveillance Subsystem will consist of three preparation steps and a series of report formatters. The function of this subsystem is to provide exception reports of abnormal system use by specifi...
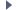 Trace Subsystem Functional Description
Trace Subsystem Functional Description- The function of the trace subsystem is to produce from the SMF records a detailed, time-sequenced log of activity by (or on) a selected entity. The Security- Trace Subsystem will accept parameters ...
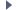 Integration Of Subsystems
Integration Of Subsystems- The scope of this task depends on the system environment in which the security officer subsystems will be placed. If the programs are placed on the VM system, then one or more JCL sets (procedures) ca...
