Gaining Access To The System - External Penetration
Description
This section is from the book "Computer Security Threat Monitoring And Surveillance", by James P. Anderson.
Gaining Access To The System - External Penetration
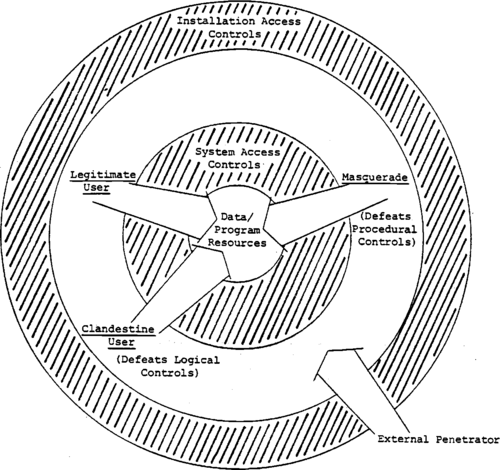
In the context of this report, the term "external penetration1' is not confined to the usual case of an outsider attempting to gain access to a computer resource in an organization of which he is not a part. The term is meant to convey, in addition to the previous case, the notion of an employee of the organization who has physical access to the building housing the computer system but who is not an authorized computer user. These cases are of general and specific interest in that they represent in some ways the extremes of the problem of gaining access to a computer.
The true outsider has the most difficult task in some ways, if the only means (terminals, RJE stations, etc.). of accessing a computer are physically co-located with the computer in the same buildings. Where access to computer resources is granted through wire communications, the external penetrator has a substantially easier task in attempting to gain physical access. For those systems and networks has merely to wire tap a communication line to effectively gain use of the targeted system.
Penetrator Not Authorized to Use Data/Program Resource | Penetrator Authorized to Use Data/Program Resource | |
Penetrator Not Authorized Use of Computer | Case A: External Penetration | |
Penetrator Authorized Use of Computer. | Case B: | Case C: Misfeasance |
Figure 1. General Cases of Threats
Threat Representations.
The individual with physical access to the building housing the computer systems or its terminals does not have to -resort to such exotic methods. However, it may be more difficult for such an individual to gain access to use the system without attracting attention. Whether or not this is true in any specific instance is in part a function of how mature the insolation is and in particular, whether or not there are many terminals for use of the computer resources.
In the case of the user with physical access to the building housing the computer systems, there is a possibility of additional information that may be useful to correlate for security purposes. As an example, in those buildings that employ security logging or . building access systems that record the time and point of entry and exit of all individuals, it would be possible for detected security incidents to be correlated with individuals who could conceivably be involved in the incidents.
In case of unprotected communication lines, there is opportunity for individuals to attempt to gain use of computer systems by trail and error attempts at logging on. Records of the log on attempts if collected, would provide security officers with a substantial warning of unauthorized activity, and identification of at least the location from which unauthorized access is being attempted.
In most systems such data is not collected. This is because the systems are generally large with a laxge number of users, and recording the presumed attempted logons would consume too many system resources to warrant their acquisition.
In addition there is a potential problem created by recording in the audit data unsuccessful logons if those logons contain the password or other user authenticator. The danger is that the audit trail will contain paxtial or complete user authenticators or passwords from legitimate errors made by authorized users as well as the unsuccessful external penetration attempts. This is not to say such-data should not be collected, it is only to point out that in the collection it is possible that a greater danger is created.
Auditing of attempted logons can include identification of the terminal, the port through which the terminal is connected to the system, and the claimed identity of the user and the like. If the assets required it, it would be possible to trigger an immediate exception report to the security officer or other operations personnel if the number of unsuccessful longons from a given port number exceeded some threshold over time. The cost of this idea is the additional complication of maintaining logon records or even extracts from logon records on a per-port basis when the number of ports or the number of potential users of the system is extremely large. Note that the external penetrator threat translates into an internal threat as soon as the installation access controls have been penetrated.
Continue to:
- prev: Threats
- Table of Contents
- next: Internal Penetration
