Surveillance Subsystem Functional Description
Description
This section is from the book "Computer Security Threat Monitoring And Surveillance", by James P. Anderson.
Surveillance Subsystem Functional Description
The Surveillance Subsystem will consist of three preparation steps and a series of report formatters. The function of this subsystem is to provide exception reports of "abnormal" system use by specified individuals.
The function of the first step of the surveillance subsystem is to extract from the dump data set all relevant SMF records associated with a list of users making up the (a) "watch list". The selected SMF records are collected in a single data set where they are sorted in time-sequence order by user-id.
The sorted selected records will be processed by the next step to create one record per job or session. The record will be identified by the user-id, and the list of data sets or files referred -to as a job/session characteristic.
Detailed measures of time, I/O activity, and the like, associated with the job/session (as described in section 3), will be collected in summary form in the job/session record.
(NOTE: Some of this data was apparently being collected in customer-developed SMF records type 210 in 1978 and 1979. If these records are still being collected, this step may merely be an adaptation of the program that produces the type 210 records.)
The job/session records will then be posted in user-id, job/session characteristic order for the update step to follow.
The update step matches job/session records against history records to: determine whether individual job/session records are within statistical "normality"; accumulate additional data to refine the statistics; look for single "abnormal" events (illegal logons, single parameter absolute values exceeding arbitrary thresholds, etc.); create "new" history records (existing user, new job/session characteristic or totally new user); drop "old" history records for lack of activity.
The update step will produce an exception file with all major exceptions reported at least by type (e.g., values exceed absolute limits; values exceed statistical limit; new records added; old records dropped for lack of activity; etc.).
The final step(s) are a set of report formatters that select a particular exception type and edit and format a report for that kind of exception (see Figures 6, 7, 8, and 9 for examples).
Tasks
Tasks | Level of Effort (man-weeks) | Elapsed Time (weeks) | |
I. Design Job/Session Record, History Record, and Exception Records II. Design Selection Step Program III. Design Job/Session Summary Program IV. Design Update Program V. Design Report Programs VI. Code and Test Selection Step VII. Code and Test Summary Step VIII. Code and Test Update Step IX. Code and Test Exception Reports (approximately 4) TOTALS | 4 | 4 | |
1 | 1 | ||
2 | 2 | ||
2 | 2 | ||
1 lor 4 reports) | 1 | ||
2 | 2 | ||
4 | 4 | ||
8 | 8 | ||
2 | 2 | ||
26 | 26 | ||
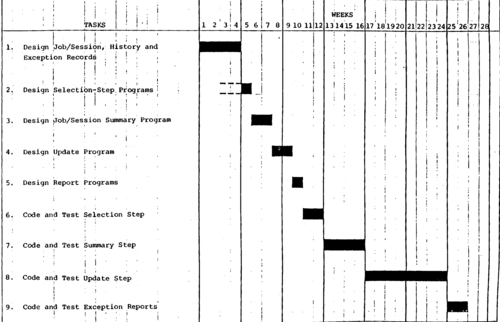
Summary Task Schedule For Security Surveillance Subsystems.
Continue to:
