Trace Subsystem Functional Description
Description
This section is from the book "Computer Security Threat Monitoring And Surveillance", by James P. Anderson.
Trace Subsystem Functional Description
The function of the trace subsystem is to produce from the SMF records a detailed, time-sequenced log of activity by (or on) a selected entity.
The Security- Trace Subsystem will accept parameters specifying the type of entity and the time scope of the trace. The trace report will be fixed for a given type of entity.
Parameters to the trace should include:
Type of entity (job-id, user-id, data set, device-id, etc.);
Time parameters: start date (if omitted - today) [end date] (if omitted - today) start time (if omitted - 00:00:00) [end time] (if omitted - 23:59:59)
As long as the times specified are increasing (and not overlapping) , it. should be feasible to trace multiple time ranges in a single pass of the "raw" SMF data.
Some time parameters might look like: 3/18/80 3/18/80 1600 3/18/80 - 3/20/80 1600
3/18/80 1600 - 1830, 3/20/80 14:30 ...
The trace records will have a standard part, then specific information that is appropriate to the record. A sample trace might look like:
Trace For User Jones.J ≪ Date (Or Date Range) >
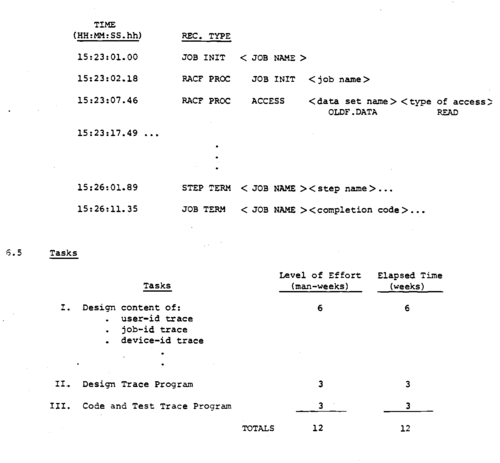
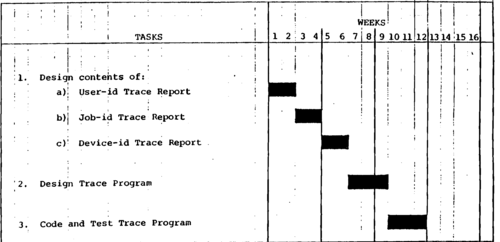
Summary Task. Schedule For Security Trace Subsystem.
Continue to:
