Integration Of Subsystems
Description
This section is from the book "Computer Security Threat Monitoring And Surveillance", by James P. Anderson.
Integration Of Subsystems
The scope of this task depends on the system environment in which the security officer subsystems will be placed. If the programs are placed on the VM system, then one or more JCL sets (procedures) can be used to permit tha programs to work with current SMF data (SYS1.MANX, SYS1.MANY data sets) or the dump data sets (SMF.DAILY.DATA) or the weekly data sets (SMF. WEEKLY .DATA). Allocation of the correct data sets can be done from the date parameters to the trace programs. There is no particular allocation required for the surveillance subsystem.
If the security officer surveillance subsystem(s) is placed on a standalone minisystem (for example), there is some action needed to either copy the entire dump data set to the minisystem (not recommended due to its size) or run the job/session select program on VM to produce a data set that will be brought over to the mini for processing.
Since access to current and recent SMF.DAILY.DATA and SMF.WEEKLY.DATA sets is needed for the trace function, and since at least the surveillance subsystem selection step must access the current SMF .DAILY .DATA, it appears that the security subsystem(s) should be placed in/on VM.
Tasks | Level of Effort (man-weeks) | Elapsed Time (weeks) |
I. Define Integration Requirements | 2 | 2 |
II. Code and Test Procs for Integration | 2 | 2 |
TOTALS | 4 | 4 |
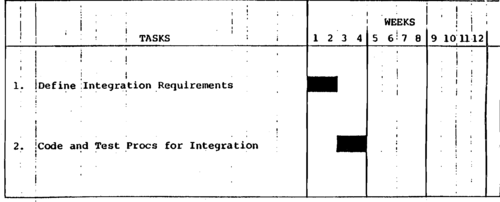
Summary Task Schedule For Integration Of Security Subsystem.
Continue to:
