Monitoring Files
Description
This section is from the book "Computer Security Threat Monitoring And Surveillance", by James P. Anderson.
Monitoring Files
Producing the records necessary to monitor use of files or other objects in a system is similar to that outlined above for monitoring users activities in a system. The principal difference is that fact that the element being sorted is the 'file', and the records being kept are on a per user basis. In some ways the files are a little more complicated than the users activities files in that multiple accesses to the same file in three or four different runs are to be treated in some sense differently, particularly in terms of the amount of data read from or written to the target file.
The file or device monitoring may require more than one pass of the audit file in order to collect the necessary information. As an example, if one wanted to record against a particular file, the users identifier and the session statistics associated with that reference to that file, it may be necessary to first pass the audit data file looking for those user identifiers or other session identifiers that are associated with its reference, make a list of those and then on a second pass of the audit data file collect the session records necessary to produce session summary statistics to be recorded against the file name. An example process flow is shown. Figure 5. Quite obviously these procedures vary as a function of the details of the type of audit trails being taken and the kind of monitoring that one attempts to perform on the specific objects.
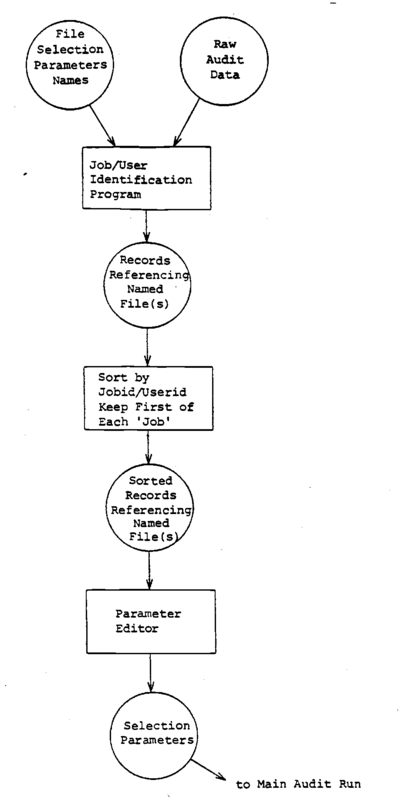
Figure 5 Processing To Audit File Use.

Transaction Records Exception Report.
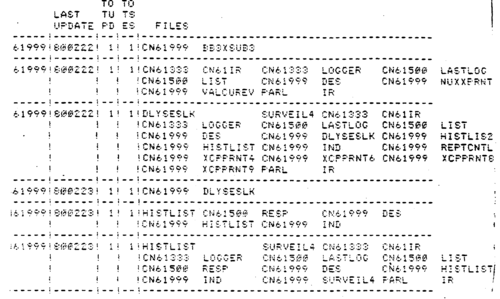
Figure 7 History Records Dropped For Lack Of Activity.
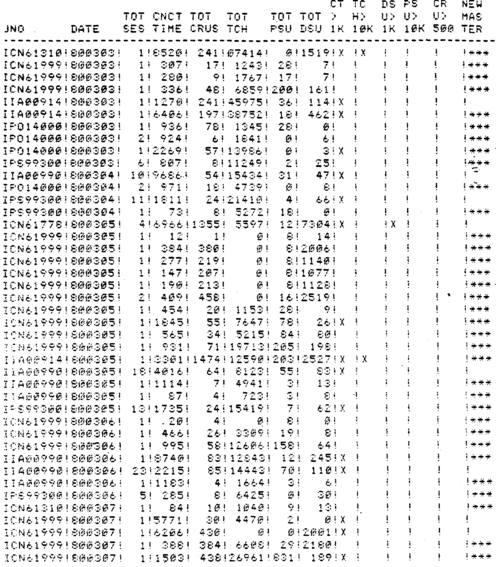
Figure 8. Session Records exception Report.

Figure 9 New Master Records.
Continue to:
- prev: Structure Of A Surveillance System
- Table of Contents
- next: Adapting To SMF Data. Relevant SMF Records
